Why Seculert?
Corporate boards and CISOs now well understand they most likely have active attacks resident on their networks stealing confidential information and intellectual property. Prevention systems have known failure rates based on regular breach disclosures. Cyber-security teams operate in an environment of increasing uncertainty as attacks have become more sophisticated and stealthy. This issue is compounded by the fact that the primary “post prevention” tools and processes are labor intensive in an environment where sufficiently skilled labor is unavailable at any price.
Seculert Approach
Seculert was founded on two core beliefs:
1-Cyber-criminals have historically and will continue to defeat prevention systems, but they also inevitably leave behind evidence of their current presence, capabilities, and intentions.
2-The only way to find that evidence quickly and accurately is to collect vast quantities of domain specific and external data and analyze it using automated detection engines that leverage the computing and storage capabilities of the cloud.
These two beliefs brought Seculert early on to a cloud based architecture that performs all of the analytics necessary to find new attacks without deploying new hardware, new software, or changes in SOC workflow. Seculert collects massive amounts of traffic data (both internal historical data and external contextual data) and performs all of the required analytics in the cloud. Not only does this deliver faster, more accurate reports of new attacks, it does so for a fraction of the cost of premises based and hybrid solutions.
The benefits of this approach accrue to both SOC operations and executive management. For SOC operations automating the detection process removes much of the pressure generated by the security analyst skills gap. One CISO is on record as claiming that installing Seculert was, “…worth hiring three extra security analysts for a fraction of the cost and these three never sleep.” Second for the SOC team, automating the attack detection process greatly reduces the time required to find sophisticated attacks from weeks or months to days. Finally, the SOC team gets the benefit of pumping the Seculert attack reports directly back into their prevention systems to make them more effective.
For executive management the Seculert Platform provides unprecedented visibility on overall security system performance. As noted above, prevention systems will fail a material per-cent of the time. Seculert research indicates at least 15% of the time. The challenge now is to determine when and how.
Seculert provides regular detailed reports covering:
- Key findings of what is attacking the enterprise and how the overall security system is performing
- Breach analytics depicting attack activity and a breakdown of incidents according to the state of their containment
- Incident response benchmarks illuminating a customer organization’s incident response performance, compares it to similar companies and compares it to prevention performance of different secure web gateway vendors.
AND all of this gets delivered as a service with no new hardware, software, or human resources required.
Technology Overview
Automated Attack Detection Platform
Seculert’s solution is built upon a cloud-based architecture that combines a number of technologies to provide an automated attack detection platform. It starts with Big Data collected from an organization’s firewalls and/or proxy devices, combining it with data collected across the Seculert network and proprietary data developed by Seculert’s Research Lab. Data is also collected from Seculert’s Elastic Sandbox. This data is analyzed using advanced data science to identify anomalous behavior. Seculert’s malware experts create profiles and supervised machine learning algorithms that then powers Seculert’s Automated Attack Detection Platform.
To learn more about the details driving the Seculert platform, select any of the links below.

Seculert Analytics
The term “Analytics Driven Cyber-security” or ADCS, was originally coined by ESG analyst John Oltsik in the spring of 2015 but is only now getting the attention it deserves. It well captures what we’re about at Seculert and will almost certainly be one of the next “big things” in cyber-security…
The reason ADCS will be of increasing importance is that nearly all sophisticated enterprises understand that their real-time prevention systems will fail them periodically no matter how well they are designed and operated and that new approaches are required to address the current threat landscape. Recent Seculert research indicates that most prevention solutions fail at least 15% of the time and, in the case of web gateways, 90% failure rates are not uncommon.
Seculert’s approach to ADCS starts by ingesting log data from either Next Generation Firewalls and/or gateway proxy devices. This is then combined with proprietary contextual data that includes unique malware profiles developed by Seculert’s Research Lab and threat data from the company’s botnet interception network. It also includes data from across the Seculert network that provides visibility on new and emerging threats and data on how commonly deployed prevention technologies are responding to those threats. All of this data is then processed using Seculert’s supervised machine learning engines to identify anomalous outbound traffic patterns. Such patterns indicate that malware has infected devices and is communicating with its
Data analysis is only as effective as the expertise that it embodies. Seculert’s malware experts work together with experts in statistical analysis and Big Data Analytics to create the malware profiles and create supervised machine learning algorithms that power Seculert’s cloud-based Automated Attack Detection Platform. Even in the cloud, the requisite statistical analysis of Big Data is very challenging. Today’s statistical packages generally assume that the data set can fit in the memory of one computer. Seculert has developed proprietary techniques for performing scalable machine learning using Hadoop, Spark, and Amazon’s Elastic MapReduce
If this seems like a lot of effort to go through to improve attack detection it is. Just assembling the team qualified to do it can take years…but, it’s worth it. It’s worth it because the net effect is regular reports on verified “True Positive” attacks. As we like to say, Seculert provides answers, not clues to new attacks and does so without requiring any new hardware, software, resources, or changes to existing security procedures.
So, there is no reason to wait to see if Analytics Driven Cyber-security can improve your security posture. The Seculert Automated Attack Detection Platform (and all of its ADCS technologies) is available today.
The Keys to Your Success
Dashboards & Executive Reports
At Seculert we’ve always believed that the key to effective cyber-defense is visibility, specifically visibility of two things:
- What’s currently attacking the enterprise and how is it behaving (or mis-behaving)
- How is the existing security infrastructure responding to those attacks and limiting the damage done by them.
The first of these items is primarily of concern to SOC teams and security analysts whether in-house or outsourced MSSP analysts. The key to success for these teams is achieving rapid visibility on new attacks, and providing enough information to enable rapid and accurate remediation.
The second of these items is of concern primarily to senior security managers and executives. The key to success is being able to measure overall security system performance and identify systemic weaknesses that require further investment or technology upgrades.
Seculert provides unique visibility to both SOC and executive teams.
Protect Your Organization
Analyst Dashboards
Seculert Automated Attack Detection Service provides browser-based dashboards for the security analyst to rapidly respond to cyber attacks and for the IT executive to gain visibility into the cyber threats successfully targeting their organization and benchmark effectiveness of the response process.
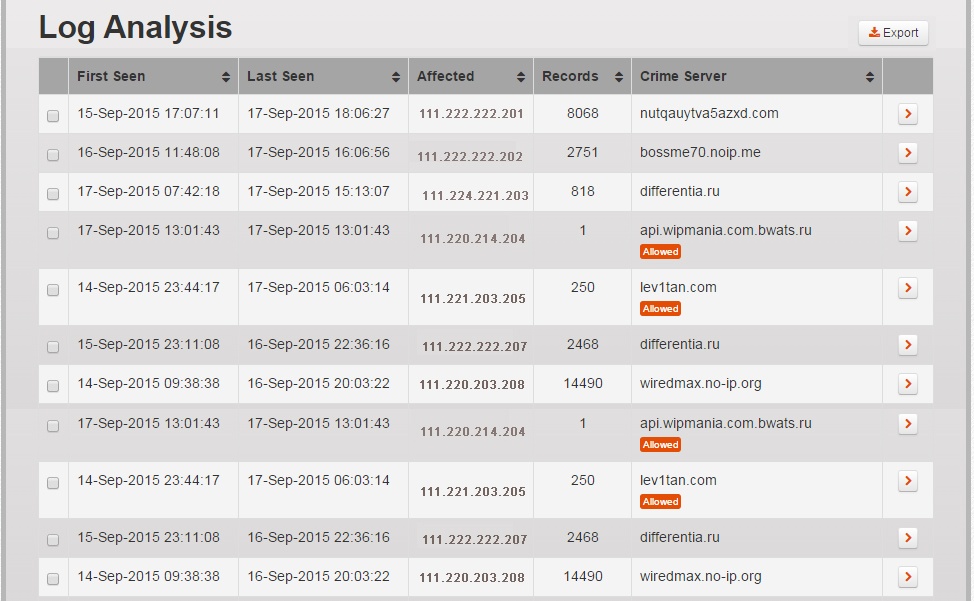
When responding to cyber attacks security analysts need to be able to prioritize and to minimize time between alert and containment. Through the Incident Review workflow, analysts can quickly triage Seculert incidents and then conveniently drill down into to the incident details. Key information helps the analyst quick triage: Malware riskiest capability; time infection was last seen or detected; and duration & number of communication records. On the dashboard, Incidents where malicious communication with a C&C host was ‘Allowed Through’ are marked as prioritized.
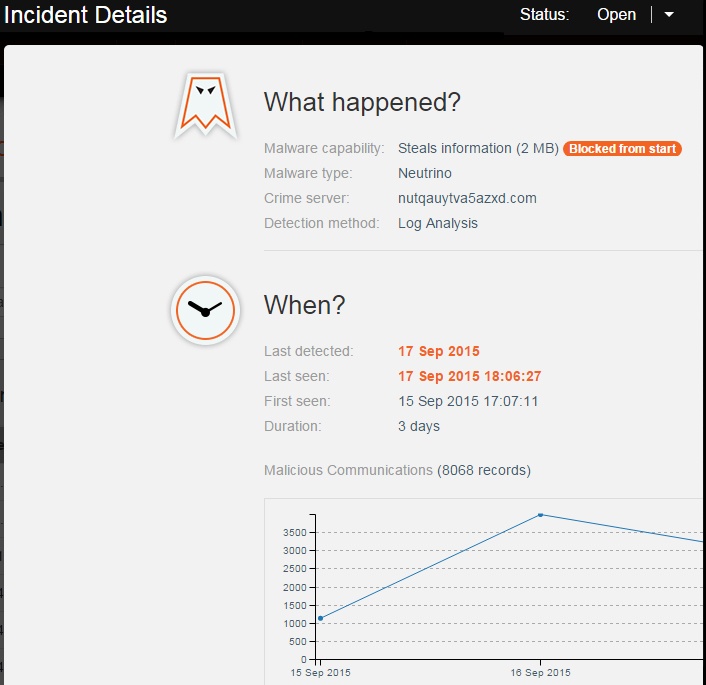
A drill down to Incident Details tells provides the answer to:
- Who was affected – machine IP, name, location and user name
- What happened – Malware type and capability, C&C host, whether the malware enabled anomalous communications
- When – Timeline of the incident
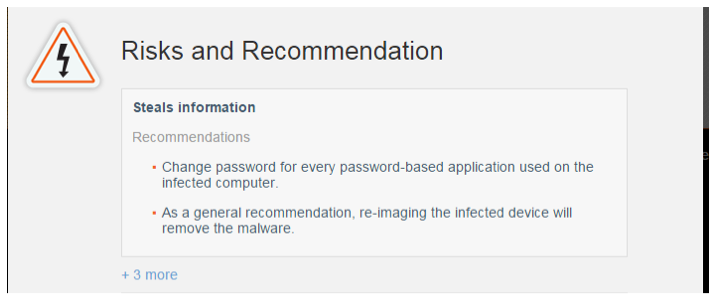
The dashboard also has a section on 'Risks and Recommendations' to help prioritize the incident and help the analyst plan a response.
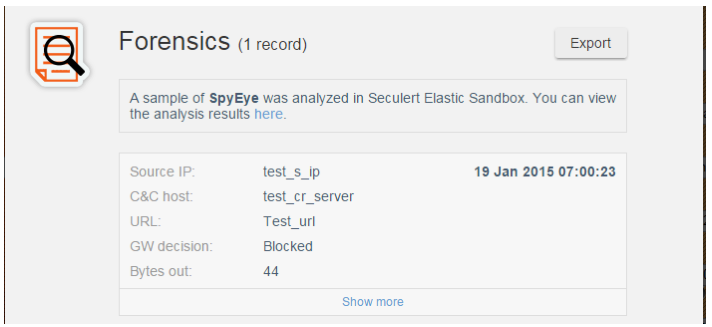
A ‘Forensics’ report provides the raw log data or intercepted Botnet data, and a sandbox analysis a sample of the malware (when available).
These dashboards provide the security analyst and the IT executive access to the tools they need to best protect their organization.

Breach Response Automation
Quickly Respond and Protect
The lack of skilled resources is significantly impacting cyber-security teams today. They find themselves in a state of uncertainty, lacking the visibility or time to know which if any of their devices, users and data have been compromised. Manually sifting through the countless numbers of alerts / Indicators of Compromises the security team faces on a daily basis to detect real attacks takes time. Time in which successful attacks that have breached the perimeter are compromising the organization’s security.
The lack of skilled resources is significantly impacting cyber-security teams today. They find themselves in a state of uncertainty, lacking the visibility or time to know which if any of their devices, users and data have been compromised. Manually sifting through the countless numbers of alerts / Indicators of Compromises the security team faces on a daily basis to detect real attacks takes time. Time in which successful attacks that have breached the perimeter are compromising the organization’s security. Unfortunately, as cyber attacks rise in frequency and sophistication, the problem cannot be solved by hiring more security analysts even if they were available. The solution is first to assist the security analyst by automating the detection of breaches – providing the analyst answers, not clues. And then automate the response where possible – either by delivering Incident Response ready reports of attack directly to the SOC’s remediation process OR by using the Seculert Protection API to provide actionable information to existing security devices and applications.
Seculert’s automated detection capability was built by a team of world-class malware engineers and big data specialists. The detection capability is built around a supervised machine learning engine that look for anomalies in log data based on rules developed by the team. The machine learning engine runs on a massively scalable cloud platform that can process more data much faster than any on premises solution.
Automating the profoundly manual process that a SIEM based detection team must pursue dramatically reduces the amount of labor respond to a breach. And, because the automated detection capability provides answers, not clues, it automates the “investigate” stage and allows to proceed directly to remediation.
Seculert takes automation one step further. Using the Seculert Protection API, organization can automatically provide dynamic threat intelligence to an organization’s existing security devices. For example, the API can provide information about blacklisted IP addresses and domains, newly detected malware profiles.
Seculert’s Automated Attack Detection Platform not only reduces the time and effort to detect a breach, it improves an organization’s ability to quickly respond and protect against similar breaches.
Big Data Analytics
Identify Advanced & Sophisticated Threats
Collecting and analyzing massive quantities of data (also know as Big Data) is core to how the Seculert Platform automatically detects attacks. The analysis of Big Data across a wide range of sources allows the Seculert platform to identify advanced and sophisticated threats by highlighting anomalous behavior signals amidst a large amount of noise
To meet the extensive compute requirements for Big Data analytics, the Seculert Platform leverages the elastic resources and distributed processing power of the cloud. Even in the cloud, the requisite statistical analysis of Big Data is very challenging. Today’s statistical packages generally assume that the data set can fit in the memory of one computer. Seculert has developed proprietary techniques for performing scalable machine learning using Hadoop and Amazon’s Elastic MapReduce.
Key to the success of the Big Data analytics is the sources of information. They include the traffic logs, proprietary attack profiles, results from Seculert’s Elastic Sandbox analysis, Botnet Interception data, and publically available threat intelligence feeds.
Network Traffic Logs
The Seculert Platform collects traffic logs from firewalls, proxies and other network devices across all of Seculert’s customers over a significant period of time. Machine learning leverages this massive amount of data to identify malware profiles at the user, organization, industry, and regional levels.
Elastic Sandbox
Whenever the Seculert discovers a suspicious and previously unknown executable, it is executed in the Elastic Sandbox to determine whether it contains malware. Throughout the execution, the Seculert Platform records all of its network communications and uses Big Data Analytics to identify its behavioral profile and command and control servers. The results of this analysis are then added to the Seculert’s malware profile big data store.
Botnet Interception
The Botnet Interception module joins hundreds of active botnets and listens in on traffic for as long as necessary. It continuously generates large amounts of data which is stored in the cloud and processed using proprietary big data analytics in order to detect all of the infected devices both inside and outside of the corporate network.
Publically available and proprietary threat intelligence feeds: Seculert’s Big Data store also includes information from threat feeds that identify bad IP addresses, malware signatures, and other indicators of compromise.
It is this wide range of sources of information along with the processing power of the cloud and the malware expertise of Seculert that powers the Seculert Automated Attack Detection Platform and provides security teams the answers they need.

Application Programming Interface
Seamlessly Extend Your Security Perimeter
The Seculert’s Application Programming Interface (API) is designed to integrate existing security solutions and applications with the Seculert Automated Attack Detection Platform. With Seculert’s API enterprises can now seamlessly extend the security perimeter with the dynamic threat intelligence provided by Seculert’s cloud-based platform.
Seculert’s API is designed to enable Seculert’s technologies to directly interact with existing on-premises gateways, proxies, NGFWs, and SIEM systems. Designed from the cloud down to be easy-to-use, flexible and powerful, Seculert’s Protection API transforms existing security systems into a comprehensive attack detection solution.
Below are just a few of the many benefits of deploying Seculert’s API:
- Keep perimeter prevention systems up-to-date by easily synchronizing blacklisted IPs and domain names
- Retrieve log analysis results, providing additional insight into malicious network activity
- Update prevention systems with the latest attack profiles from Seculert
- Deliver dynamic forensics on botnet communications to perimeter security systems to block further attacks
- Correlate events of compromised endpoints found by Seculert with other security alerts on SIEM systems
Executive Reports
In addition to the SOC analyst dashboards, the Seculert platform provides security executives with unprecedented visibility on overall security system performance. The report delivers three different types of actionable data:
- Key Finding: What was attacking the devices and users on the network, what got through, and how the security system responded
- Breach Analysis: How active were the attacks that breached the perimeter and what did they do or attempt to do
- Incident response benchmarks: Comparison of how each Seculert protected enterprise did handling current attacks and comparing that response vs. external and industry peers.
Whether an enterprise is running their own SOC or relying on an MSSP, the Seculert platform provides visibility on how prepared they are to deal with the current threat landscape.
The ‘Key Findings’ report summarizes the extent of attacks and how well they were contained.
In the example, Seculert identified 572 infections, 17,000 malicious communications, 260 Gigabytes exfiltrated data. The longest infection lasted 162 days and 59% of infections were 'Allowed Through'.
The ‘Incident Analysis’ dashboard drills down into attack activity and breaks down incidents according to their state of containment. In the example, the graph shows number of infected assets over time (orange), number of assets sending malicious communications (gray).
The pie chart shows that 17.5% of incidents, malware was able to communicate with a malicious Command and Control host (red).
In additional 40.7% of incidents, malicious communication were eventually contained by being blocked by the gateway, or remediated (orange). In the remaining 41.8% of incidents, malicious communication was blocked by the web gateway from the first attempt.
The ‘Incident Response Benchmarks’ dashboard benchmarks an organization’s incident response, compares it to similar companies, and compares performance of different secure web gateways.
In the example, on average 19 incidents were remediated per week. ‘Infected Asset Remediation’ shows the amount of 'Open' incident cases (orange) and the amount of incidents remediated (blue) over time.
‘Infection Days’ shows distribution of incident duration until remediation and compares you to other companies. For instance, 72% of incidents were remediated in less than 5 days. ‘Infection Rates’ compares proportion of infected assets in the network vs. other Seculert customers.
‘Gateway Prevention Performance’ compares proportion of infected assets that were 'Allowed Through' vs. other Secure Web Gateway vendors that Seculert analyzes.