When responding to cyber attack incidents SOC teams need to be able to prioritize and to minimize time between alert and containment.
Through an Incident Review workflow, SOC users can quickly triage Seculert incidents and drill down to details easity.
Pertinent information helps accelerates triage: Malware riskiest capability, time infection was last seen or detected, duration, and number of communication records.
Incidents where malicious communication with a C&C host was ‘Allowed Through’ are marked as prioritized.
You can also navigate between different Incident Zones: Internal, Remote Access, Partners, and Customers and filter incidents.
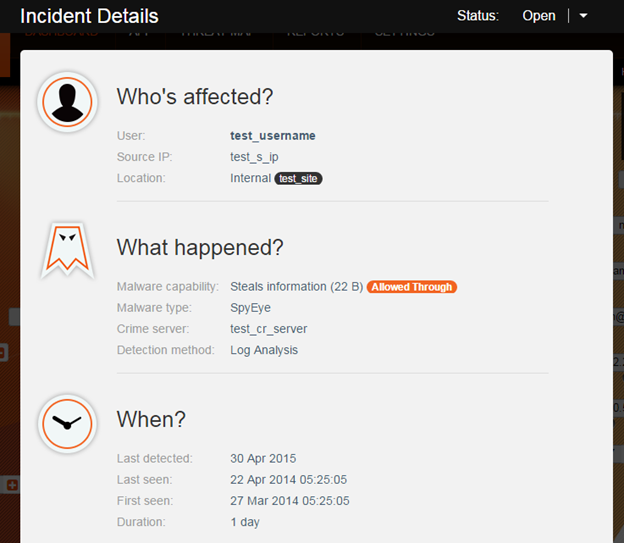
A drill down to Incident Details tells the story through answering ‘Who?’, ‘What?’, ‘When?’ questions.

‘Who’s affected?’ reports machine IP, machine name, machine location and user name.
‘What Happened?’ reports malware type and capability, C&C host , was there a successful malicious communication.
‘When?’ shows incident timeline.
'Risks and Recommendations' help further prioritize incident alert and plan response.

‘Forensics’ reports the raw log data or intercepted Botnet data, and sandbox analysis a sample of the malware (when available).
It is important to note that in order to view all the records, you should use the ‘Export’ button.
In addition, since the sandbox analysis is of different malware sample than the one infecting your network, the IoCs might be different from the actual ones in the incident.

For more information about the new Incident Review, login to the Seculert portal or contact your account manager today.