latest insights
seculert blog


An Acquisition is Akin to a Rollercoaster Ride
-
Seculert Was Acquired By Radware On January 31, 2017 - An Industry Leader in Cyber Security. WHAT A RIDE!
Since completing the Radware acquisition of Seculert few days ago, I understand now more than ever how a rollercoaster ride compares to a business endeavor. It is exhilarating and frightening at times, but overall, very much worth the time I spent in line to take that ride.
read moreLet’s Hack an Election, Shall We?
With the election only a week away, the discussion about how the upcoming U.S. presidential election may or may not be “rigged” is being closely watched. ‘Election hacking’ reports from CNN, the Washington Post, and even the candidates themselves provide yet another debate platform regarding the possibility of corrupted election results. For the purpose of this blog let’s set aside the fact about our national election system is far too distributed for any widespread national vote theft to occur and explore the more likely technological aspects of “hacking an election” through swing states...and what we know through Seculert Labs analysis.
read more
Nymaim: Deep Technical Dive - Adventures in Evasive Malware
Nymaim is mostly known worldwide as a downloader, although it seems they evolved from former versions, now having new functionalities to obtain data on the machine with no need to download a new payload. Some of the exported functionalities allow harvesting passwords and browsers data from the machine, hidden on the file system until communication occurs. Payloads downloaded from the C&C are not saved locally on the machine but instead are loaded dynamically to memory with a unique internal calling convention.
One of the signature features I noticed when I began analyzing the Nymaim payload were the novel anti-reverse engineering and obfuscation techniques. Frustrating the analyzer many different code pieces for the same function requires piecing them together in order to fully understand the code. Most of the code is heavily obfuscated using ‘spaghetti code’ methods but we'll dive into that in a 1 (bit).
read moreUrsnif: Deep Technical Dive
While attack tools around the world are stealthy and stay under the radar, we at Seculert examine many different malicious tools. This is done to stay at least one step ahead of the attackers, and improve our advanced analytics technology to detect their artistic evasive techniques.
read morePossible Nation State Attackers ProjectSauron to Covertly Eavesdrop on Government Organizations
InfoSec professionals know that most so-called Advanced Persistent Threats (APTs) are, frankly speaking, not truly APTs. But every now and then, a real persistent attack using different advanced evasive techniques emerges on the cyber threat landscape, and it’s critical for organizations to sit up and take notice. And the most recent addition to this Most Unwanted List is courtesy of a hacker group calling itself ProjectSauron.
read moreSecurity Analytics: A "Top Four" Topic At Black Hat
A significant and respected collective of global IT security professionals congregate in the U.S. twice yearly, for RSA during the mild and temperate San Francisco winters, and later for Black Hat & Defcon, annually held in the sweltering and abysmal heat of a Las Vegas August.
Unfriendly outdoor temperatures aside, last week's #BHUSA 2016 featured all of the usual demonstrations of 'how to hack anything with a network connection', keynotes by industry luminaries, and parties (it is Vegas after all). The problem with being on the ground at Black Hat is that no matter how much effort you expend, it's only possible to see and absorb a portion of it - even if you spend every waking hour in sessions or on the show floor. Thus, I've made it a ritual to review and read what other attendees had to share in the aftermath of these conferences.

451 Research Report on Javelin Attack Simulator
Those of you who follow this space may likely have noticed Seculert's announcement of a significant product line extension 60 days ago. The "Seculert Javelin Attack Simulator" is the culmination of our efforts to extend a critical piece of the knowledge embodied in Seculert's "Attack Detection Platform" to a wider audience.
read moreThere's a hole in my bucket, dear Liza
Say you’ve got a bucket with some holes in it. Much like Henry in the famous song, you would really like to mend them. But, before you actually mend the holes you would need to discover whether you do have open holes, or maybe all of them are already mended.
Similarly, as the person in charge for the security of your enterprise network, you would most likely want to know if your web gateway (whether it’s a proxy, a secure web gateway, or next gen firewall) will be able to block the attackers’ tools from communicating back to the attackers. Because, we all know by now that eventually an attacker will be able to get inside your network and compromise at-least one of the devices. In fact, in our recent research we discovered that an average of 2% of the devices in a typical enterprise environment are already compromised.
This is exactly why Seculert created Javelin. Javelin is an attack simulator, which will “pour water” across your network environment and will try to reach out to places which your web gateway should have already blocked.
In order to do that, we have picked the top and latest bad actors that we could find by analyzing the traffic logs of our 2 million enterprise users. We then safely simulate the outbound communication behavior of each of the tools those bad actors are using in their attacks. You then have instant visibility on whether your web gateway was able to block those potential attacks or not. This is all done without the need to install any software or hardware.
If your web gateway is configured properly, and it is really is able to protect you against the latest attacks, you should see a result similar to this:
2016: Smarter Bad Guys, Better-Armed Good Guys
By InfoSecurity Magazine on November 25, 2015
read more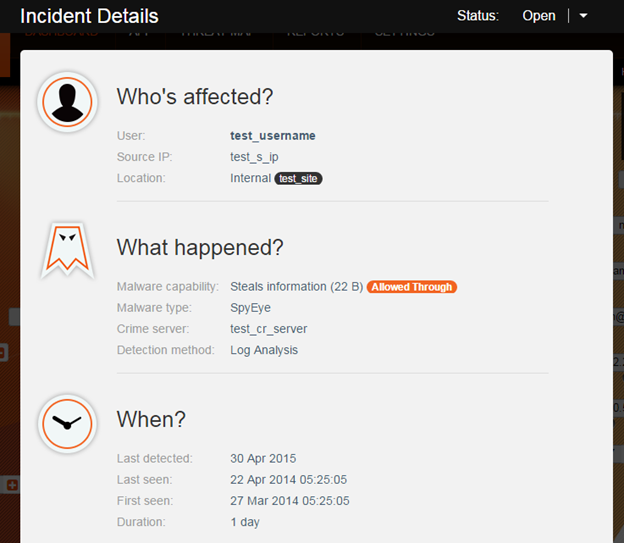
Seculert Revamps Incident Review Workflow in Seculert Web Portal [Product Update]
When responding to cyber attack incidents SOC teams need to be able to prioritize and to minimize time between alert and containment.
read more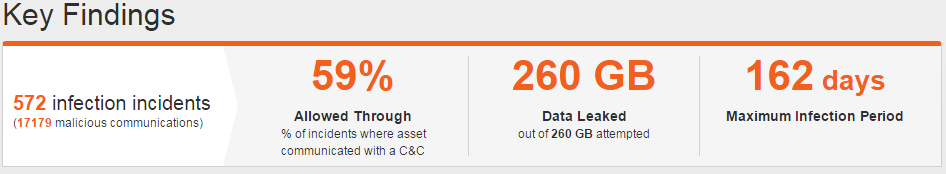
Seculert Emphasizes Visibility for Security Executives [Product Update]
Through a new dashboard, IT executives can gain visibility into the cyber threats successfully targeting their organization and benchmark effectiveness of their response processes.
read moreWhat to Look for in Machine Learning Based Security Solutions
After a relentless stream of high profile data breaches, the spotlight is on corporations to improve their security operations. As the recent disclosure from Experian demonstrated, even enterprises with the most sophisticated prevention layers are vulnerable. Most CISOs are now searching for “post-prevention” systems that can provide visibility on active attacks that have defeated their prevention systems.
read moreDGA.Changer Playing The Imitation Game With Sandboxes
Seculert researchers closely follow the evolution of major malware families while examining the behavioral malware profiles that are a core part of our breach analytics platform. Back in 2013 I wrote about the enhancements to the DGA.Changer malware that allowed it to change its seed which in turn allowed it to connect to a different stream of domain names.
read moreNetwork Breached? Ask Yourself these 3 Questions within the First 48 Hours
In an article for Bankingtech.com, Peter Cheney, the director of cybersecurity at independent global risk and strategic consulting firm Control Risks, has identified three essential questions that he believes enterprises must ask within the first 48 hours after a network breach:
read moreNetwork Breached? Ask Yourself these Key Questions within the First 48 Hours
In an article for Bankingtech.com, Peter Cheney, the director of cybersecurity at independent global risk and strategic consulting firm Control Risks, has identified three essential questions that he believes enterprises must ask within the first 48 hours after a network breach:
read moreCybersecurity’s Weakest Link? Employees
About 15 years ago, a game show took public humiliation to new heights (or depths, depending on one’s perspective) by branding unsuccessful contestants as the weakest link in the group. They were then ushered offstage to the tune of the most soul-crushing “goodbye” in television history by the host.
read moreCyber Attacks Beating 54% of Organizations Says Survey
A survey of 500 IT decision-makers in UK enterprises (250+ employees) has revealed that 54% lack the knowledge and capacity required to thwart sophisticated cyber attacks.
read moreCybersecurity’s Weakest Link? Employees
About 15 years ago, a game show took public humiliation to new heights (or depths, depending on one’s perspective) by branding unsuccessful contestants as the weakest link in the group. They were then ushered offstage to the tune of the most soul-crushing “goodbye” in television history by the host.
read moreCyber Attacks Beating 54% of Organizations Says Survey
A survey of 500 IT decision-makers in UK enterprises (250+ employees) has revealed that 54% lack the knowledge and capacity required to thwart sophisticated cyber attacks.
read moreMalware Slips by Prevention-Based Security Software
An automated and independent malware testing service has taken a quick break from analyzing malware such as worms, information stealers, and rootkits so that it can crunch some numbers — and the news isn’t good for enterprises that rely exclusively on prevention-based security software packages.
read moreMalware Slips by Prevention-Based Security Software
An automated and independent malware testing service has taken a quick break from analyzing malware such as worms, information stealers, and rootkits so that it can crunch some numbers — and the news isn’t good for enterprises that rely exclusively on prevention-based security software packages.
read moreOn-Demand Webinar: Proxy Games - How Enterprises Remain Vulnerable to Threats
Today's enterprises still remain vulnerable to threats, in particular those companies relying on prevention-based perimeter...
read moreCyber Security Staff Salaries are Booming
As reported by the Wall Street Journal, salaries for mid-level software engineers capable of helping enterprises thwart advanced malware and prevent data leaks are booming. Add the fact that many CSOs tasked with on-boarding new talent are hindered by strict salary caps, and the problem of recruiting and retaining cyber security staff has become even more intractable.
read moreMachine Learning: The Revolution of Possibilities
Data scientists, CISOs, entrepreneurs, and everyone else who wants a snapshot of the promise and potential of machine learning should check out the stirring talk delivered by Jeremy Howard at TEDxBrussels.
read moreNew Dyre variant outsmarts AV researchers' sandboxes
Now Seculert researchers have discovered new changes that make Dyre more difficult to detect and analyze.
read moreAnti-sandbox capabilities found in Dyre malware
Seculert research discovers that a new version of the financial malware Dyre is avoiding sandbox detection by counting the number of cores.
read moreBanking Trojan Uses Simple Method to Evade White Hats’ Analysis
A new variant of Dyre banking Trojan has emerged with a simple, yet efficient trick that prevents malware researchers from analyzing it.
read moreDyre Malware Developers Add Code to Elude Detection by Analysis Tools
As more companies deploy sandboxing technology to catch advanced malware, many attackers are adding code to their program to detect if the attack running in a virtual machine.
read moreDyre Banking Trojan Counts Processor Cores to Detect Sandboxes
Researchers have come across a new version of the Dyre banking malware that leverages a clever yet simple technique to evade sandboxes and prevent analysis.
read moreDyre Banking Trojan Jumps Out Of Sandbox
A number of unidentified commercial and freely available sandboxes fail to detect a new version of the Dyre banking Trojan, which was recently blamed for more than $1 million in losses to financial institutions and enterprises. - See more at: https://threatpost.com/dyre-banking-trojan-jumps-out-of-sandbox#sthash.c0CmYihA.dpuf
read moreDyreza Banking Trojan Variant Evades Sandbox Solutions
Researchers have documented a new variant of the Dyreza banking trojan, a member of the Dyre malware family, which has the capability to evade an array of sandbox solutions.
read moreDyre Banking Trojan Counts Processor Cores to Detect Sandboxes
According to Seculert, the new Dyre sample they’ve analyzed is designed to check the number of processor cores on the infected machine. Since most modern PCs have at least two cores, a single core could indicate the presence of a sandbox. That is because sandboxes are usually configured to use only one core in order to save resources.
read moreDyre Trojan Adds New Sandbox-Evasion Feature
New tactic makes it that much harder to detect, says Seculert.
read moreNew Dyre Version- Yet Another Malware Evading Sandboxes
Last fall, we posted about the new tricks of the Tinba trojan. Now the Dyre malware, another trojan, has some new tricks of its own.
read morePerimeter Security Defenses: A Technical Review
As my colleague and co-founder, Dudi Matot, noted in his Perimeter Security Defense: Time to “Think Different”? post last week, we’ve just finished a very interesting piece of Big Data research focused on the behavior of the malware that has succeeded in infecting our customer’s networks. Just to set a little context, all of Seculert’s customers run very sophisticated, multi-layered malware prevention systems that include Next Generation Firewalls, modern Intrusion Prevention Systems, inline sandbox technologies, Secure Web Gateways, and current endpoint security. These are some of the most cyber-security oriented enterprises on earth and yet they are still finding malware infecting their networks on a daily basis.
read moreState of Perimeter Security Defenses Report
Seculert Research Finds Critical Gaps in Gateway Solutions
read morePerimeter Security Defense: Time to “Think Different”?
It was almost exactly ten years ago that U.S. Counter Terrorism Advisor Richard Clarke stood before the Congressional committee investigating the 9/11 attacks and uttered the famous phrase, “Your government failed you. Those entrusted with protecting you failed you. And, I failed you.” It was a seminal moment in America’s processing of the tragedy of 9/11 because an adult stood up and declared himself to be accountable.
read moreCurrent Threat Prevention Systems Are Not Enough Protection for Enterprises
Infected devices behind a company’s protected network can still communicate with the outside without being detected, despite properly configured perimeter defenses, show the results of a recent study.
read morePaloAlto Networks, McAfee, Websense Gateway Systems Allow Malicious Traffic to SlipThrough the Net
ZDNet by Charlie Osborne | Published: April 16, 2015
read moreSeculert Research Finds Critical Gaps in Gateway Solutions
Seculert Research Finds Critical Gaps in Gateway Solutions
Study concludes hundreds of thousands of malicious communications go undetected
Santa Clara, CA - April 16, 2015 – Seculert, the leader in automated breach detection, today released its “State of Perimeter Security Defenses Report,” identifying critical security gaps in the security strategy currently employed across the world’s largest enterprises. Seculert examined a subset of its installed base environments that included nearly 800,000 client devices, generating nearly 62 billion total communications emanating from Fortune 2000 Companies in North America.
Cyber Security Skills Shortage Growing: Schools Rush to Fill Massive Gap
As reported by The Tampa Tribune, colleges across Florida are racing to create the next generation of cyber security professionals who have the required knowledge to fight back against today’s increasingly sophisticated and well-funded bad actors. For example:
-The University of South Florida has launched the Florida Cybersecurity Center, which functions as a hub to share knowledge, resources, and training among the state’s dozen public universities. read moreSeculert’s Blog Recognized as one of the 50 Best Cloud Security Blogs of 2015

Fresh on the heels of being named as one of the 100 Coolest Cloud Security Vendors by CRN, it is my pleasure to share that Seculert’s blog has been recognized as one of the 50 Best Cloud Security Blogs of 2015by GetVoIP.
read moreThe 50 Best Cloud Security Blogs of 2015
There’s a lot going on around cybersecurity – so where do you go to get the best and most useful news on what hackers, security experts, big firms and government offices are doing, and what you can do to stay safe? Here are 50 of our favorite spots for actionable security “intel.”
read moreOn-Demand Webinar: Network Security- 100 Backdoors
On-demand webinar: Experts discuss the ways an attacker can slip by your security defenses
read moreSeculert Named to CRN’s “100 Coolest Cloud Security Vendors” List
On behalf of my colleagues worldwide, I am thrilled to share that Seculert has been named as one of the “100 Coolest Cloud Security Vendors” by The Channel Company’s CRN, which is the global online and print media leader in the IT channel.
read moreSeculert Honored as Coolest Cloud Computing Vendor by CRN
Seculert Honored as Coolest Cloud Computing Vendor by CRN
Santa Clara, CA - February 9, 2015 – Seculert, the leader in advanced breach detection, today announced it has earned recognition as one of the Coolest Cloud Security Vendors as a part of The Channel Company's CRN 100 Coolest Cloud Computing Vendors of 2015. This annual list recognizes some of the most innovative cloud companies supporting the IT channel today.
read moreThe 20 Coolest Cloud Security Vendors Of The 2015 Cloud 100
Cloud security platforms are helping organizations mitigate risks associated with using cloud-based applications and services. They can provide strong data protection capabilities, incorporating data loss prevention and data encryption and tokenization. A group of vendors provide identity and access management capabilities. Others monitor cloud-based systems for suspicious activity and provide a mechanism for policy enforcement, reporting and alerting. Some vendors are also pushing the envelope, providing SaaS-based tools for managing incident response activities, a cloud-based sandbox to analyze and identify advanced threats or track and control employee laptops, smartphones and tablets regardless of their location.
read moreOn-Demand Webinar: The SONY Breach- Detailed Review
On-demand webinar: Listen in as the experts at Seculert walk through the SONY network breach.
read moreOn-Demand Webinar: Breach Detection- The Master's Class
On-demand webinar: Listen in as the experts at Seculert walk through 3 real-world infections.
read moreHow to Find and Remove the Attacker that Has Already Passed Through Your Traditional Defenses
Learn how your corporation can definitively identify APTs that are already within your network...
read moreSeculert - A Comprehensive Platform
Learn how Seculert integrates with your existing security solutions. No hardware ...
read moreSony's Cyber-Whodunit Is a Page-Turner
Was the devastating attack on Sony strictly an inside job? Or did North Korean hackers somehow gain both the expertise and the access to carry out one of the biggest cyberheists in history? "That North Korea is involved seems implausible," said Sean Sullivan, a security advisor at F-Secure, "but we now live in interesting times, so that theory can no longer be dismissed out of hand."
The Evolution of DGAs In Malware: An Interview with Aviv Raff
A cyber threat that first reared its ugly head back in 2008 continues to evolve in some of today’s malware.
Data Breach Costs Rise 23%
The Ponemon Institute’s new “2014 Global Report on the Cost of Cyber Crime” is confirming what many CISOs and other network security professionals have been saying for months: data breach costs are on the rise.
read more4 Cybersecurity Lessons From Regin Outbreak
Symantec's discovery of state-backed malware should serve as warning to firms.
DGAs: A Domain Generation Evolution
You may remember hearing about Domain Generating Algorithms, aka DGAs, from our coverage of the PushDo malware or from the malware we dubbed DGA.Changer, or more recently from our post on the Tinba Trojan. Malware threats that contain DGAs are not new, but they are more difficult to prevent and detect.
read moreHackers Humiliate U.S. State Department
The U.S. government may be thwarting thousands of daily attempts to penetrate its IT systems, but the number of successful attacks clearly is increasing, giving the appearance that the bad guys are winning at least a few battles, if not the war. Making matters worse, the security safeguards breached are roughly the same as those used by most U.S. businesses, noted Core Security's Eric Cowperthwaite.
New Variant of Matsnu Trojan Uses Configurable DGA
The Domain Generation Algorithm (DGA) used by a new variant of the Matsnu Trojan (also known as Trustezeb) relies on an interesting technique to avoid detection by security solutions.
Matsnu Botnet DGA Discovers Power of Words
Domain generation algorithms have been botmasters’ favorite tool for keeping malware up and running—and for frustrating security researchers and detection technologies.
SECURITY INFOGRAPHIC: Why the US Needs More Cyber Security Professionals
In a blog post published in back in May, my colleague Doug McLean wrote that an enterprise’s attempt to find experienced, knowledgeable, and (reasonably) affordable Security Analysts these days is no longer a traditional human resource effort, but more like “searching for unicorns”.
read moreOn-Demand Webinar: Why Breach Detection is Your Must-Have, Cyber Security Tool
On-demand webinar: As cyber security breaches become a board-level priority, join us in learning how you can automate your breach detection system.
read moreHome Depot Traces Credit Card Data Hack To Supplier Compromise
US retailer Home Depot said it has traced the world’s second largest theft of credit card details from its systems back to a supplier’s compromised username and password.
Cousin of Bugat trojan, 'Dridex,' spreads using macros
The proliferation of the Bugat trojan, also known as “Cridex,” put the threat among the top banking botnets last year – and now researchers warn that its so-called successor, “Dridex,” is targeting users via social engineering schemes.
Attention Retailers: It's Time to Plug Those Data Leaks
The birth of e-commerce dates to August 11, 1994 — the date when what was likely the first secure transaction over the World Wide Web occurred in Nashua, N.H.
Keep Calm & Verify: How To Spot A Fake Online Data Dump
Determining whether a data dump on Pastebin or elsewhere online is legit can be time-consuming and resource-intensive. Deloitte & Touche offers tips for how to weed out the fake hacks.
Staples Falls Victim to Latest Breach
So far, the Staples breach appears to be small, affecting only 11 stores in Pennsylvania, New York and New Jersey.
Office supplies chain Staples acknowledged Tuesday it is investigating a potential breach involving credit cards used at some of its stores.
How big data fights back against APTs and Malware
How Big Data works and why is it indispensable to counter advanced threats.
read moreHow to Protect Your Money From Cyber Attacks
Aviv Raff knows a thing or two about cybersecurity. He’s chief technology officer at Seculert, which specializes in helping companies detect and stop sophisticated cyber attacks. In the wake of recent megabreaches such as the one at JPMorgan Chase (JPM), where hackers compromised personal information of some 76 million households, or Home Depot (HD), where the digital intruders got at about 56 million credit and debit card numbers, Raff says no one can afford to be complacent about digital safety. “Awareness is definitely rising, but there are people out there who still think it might not happen to them,” he says. “Everyone is at risk of being compromised.”
Poodles are attacking the Internet
There's yet another Internet bug that threatens to make your private conversations public. The new enemy: "Poodle" attacks.
YL Ventures helps Israeli startups make it big where it matters: Silicon Valley
Keep it small, move to the Valley, and reap big returns.
read moreShellshock-like Weakness May Affect Windows
In the early hours of the Shellshock vulnerability in Bash, the running joke was that Windows administrators could sit back with a box of popcorn and a beverage and watch the Linux and UNIX admins scramble about for once.
Breached Retailers Harden PoS, For Now
Yet another point-of-sale (POS) breach at a major retail chain, and the victim adds encryption.
Researchers discover Tinba variant with 64-bit support, other tricks
When the source code for Tinba – a banker trojan comprised of 20 KB of code – was made public in July 2014, there was speculation among security professionals that a new version of the malware could make an appearance with some new features.
Kill Chain, Breaches, and Staying Safe – Interview With Aviv Raff
Goodwill was the victim of a cyber-attack that lasted for 18 months before it was detected. CK Systems, a hosting provider that processed payment cards for Goodwill Industries, had intruders accessing their network from Feb. 10, 2013 until August 14, 2014. The length of this attack is seemingly outrageous, but this is a common problem when it comes to cybercrime.
Tiny Tinba Trojan Could Pose Big Threat
In July 2014, the original source code of Tinba was made public in an underground forum. This leaked version comes with complete documentation and full source code. This follows other source code leaks from much more infamous and prevalent threats, which researchers worry that attackers could use as the basis for new versions. Similar to what happened with the 2011 Zeus source code leak that then lead to the creation of Citadel.
read moreFranchising The Chinese APT
Two Chinese cyber espionage gangs known for targeting very different industries and working out of different regions of the nation actually use some of the same or similar tactics, tools, and resources in their spying operations, researchers found.
Go Big or Go Home
Big Data is altering the way organizations must manage their overall IT assets and resources, reports Karen Epper Hoffman.
Reported breaches involving zero-day bug at JPMorgan Chase, other banks
Citing an unnamed U.S. government official and other anonymous sources briefed by U.S. law enforcement, Bloomberg reported on Wednesday that JPMorgan Chase, as well as at least four other financial institutions, have been hacked.
Lessons from the JPMorgan Chase Cyberattack
JPMorgan Chase is investigating a possible cyberattack. The banking giant is cooperating with law enforcement agencies, including the FBI, to understand what data Relevant Products/Services hackers may have obtained in the attack Relevant Products/Services, according to a Reuters report.
6 Factors to consider when choosing a solution to protect your network from APTs
While the situation appears daunting, getting the protection you need isn't difficult.
read more51 UPS Stores' Point-of-Sale Systems Breached
United Parcel Service (UPS) confirmed Wednesday that point-of-sale systems at 51 of its 4,470 franchise stores were breached, resulting in the theft of credit card data involved in approximately 105,000 transactions. "Each franchised center location is individually owned and runs independent private networks that are not connected to other franchised center locations," according to UPS, in a statement.
UPS data breach: Another one bites the dust
What can brown do for you? If you’re one of the unlucky customers, the answer might be that brown can compromise your credit card information. UPS revealed that it is the latest high-profile company to fall victim to a data breach resulting from a point-of-sale system compromise.
Hackers steal records on 4.5 million patients from healthcare system
A healthcare system spanning 29 states announced on Monday that cybercriminals operating from China stole information on approximately 4.5 million patients, including names, birth dates, and Social Security numbers.
CryptoLocker victims offered free key to unlock ransomed files
Security researchers have released a tool that allows victims of the infamous CryptoLocker ransomware to unlock their computers at no charge.
Security Firm Analyzes Success of Botnet Takedowns
Israel-based threat detection firm Seculert has been monitoring the effects of the recent Gameover Zeus and Shylock botnet takedown operations, and found that the cybercriminals have already taken steps to resurrect their campaigns.
Geodo, the banking trojan with email self-spreading feature
Security researchers from Seculert firm have discovered a variant of the Cridex banking worm, dubbed Geodo, which spreads itself through email.
read moreTHIS BANKING WORM IS TURNING COMPUTERS INTO MALWARE DISTRIBUTORS
Lock up your emails and hide your bank details.
read moreEvolved Cridex cyber attack found with 50,000 stolen credentials
Criminals are using a new form of the infamous Cridex malware to automatically increase the size of their botnet empire and target enterprise customers.
read moreCybercrooks breed SELF-CLONING MUTANT that STEALS your BANK DETAILS
Fresh Cridex variant plays merry hell via email
read moreSelf-Spreading Cridex Variant Detected
Security researchers have discovered a new version of the Cridex malware that includes a self-replicating component and sends phishing emails based on a database of 50,000 stolen SMTP credentials.
read moreNew Cridex Banking Trojan variant Surfaces with Self-Spreading Functionality
In an effort to infect large number of people, cybercriminals have developed a new malicious software program that contains functionality to spread itself quickly.
read moreWorm Cridex verspreidt zich nu zelf
De nieuwste versie van de al jaren rondwarende datastelende worm Cridex is voorzien van een uiterst geavanceerde infectiemethode waarmee hij zichzelf kan verspreiden.
read moreNew Cridex Malware Uses Self-Spreading Infection Mechanism
New Version of Cridex Malware Combines Data Stealer and Email Worm
read moreEvolved Cridex cyber attack found with 50,000 stolen credentials
Criminals are using a new form of the infamous Cridex malware to automatically increase the size of their botnet empire and target enterprise customers.
read moreInfostealer Bugat resurfaces with worm component
Data-stealing malware known as “Bugat” now boasts a new capability that could quicken the trojan's profileration on users' machines.
read moreInfamous Banking Malware Adds Email-Sending Feature
Cridex -- a.k.a. Feodo and Bugat -- now has a more streamlined and automated way of infecting victims and stealing their information.
read moreGeodo infostealer gets help from worm
The distribution potential of the infamous Cridex infostealer (also known as Feodo or Bugat) just went up a notch, as a new version of the malware works in conjunction with a worm that sends out emails with a link to download a zip file containing the trojan.
read moreCridex Variant Geodo Part Trojan, Part Email Worm
A knockoff of the Cridex banking Trojan has surfaced with an appetite for more than online banking credentials.
read moreCombating APTs through detection
Read how Seculert focuses on malware presence detection in order to protect networks.
read moreCybersecurity Startup Seculert Named a Cool Vendor by Gartner, Inc.
Report recognizes company for detecting advanced threats
Santa Clara, Calif., May 8, 2014 – Seculert, a leader in advanced threat protection and anti-malware solutions, today announced it has been selected by Gartner Inc., the world's leading information technology research and advisory company, as a "Cool Vendor” in the May 2, 2014 report “Security Infrastructure Protection, 2014."
read moreECI Telecom Deploys Seculert for Complete Protection Against Targeted Attacks
Security offering brings combination of scalability and flexibility to protect company’s users and corporate assets
Santa Clara, Calif., April 17, 2014 – Seculert, a leader in advanced threat protection and malware solutions, today announced that ECI Telecom, a leading provider of telecommunications solutions chose Seculert to ensure the company is protected against advanced persistent threats (APTs).
read moreTarget Ignored Data Breach Alarms
Target's security team reviewed -- and ignored -- urgent warnings from threat-detection tool about unknown malware spotted on the network.
read moreCriminals rush to exploit IE 0-day before the announced fix
Last week Microsoft has announced that today's Patch Tuesday will include a fix for the critical IE zero-day vulnerability that was found exploited in watering hole attacks earlier this year - and none too soon
read moreAsk A VC: YL Ventures’ Yoav Leitersdorf On The Cyber Security Opportunity
In this week’s episode of Ask A VC, we hosted YL Ventures’ Yoav Leitersdorf in the studio to talk about cyber security, innovations in Israel and more.
read moreSeculert Delivers Advanced Threat Protection as a Cloud-based Solution
Two months since the news of the massive Target breach broke, reports are starting to reveal bits and pieces of how the perpetrators were able to get a foothold inside Target’s point of sale system
read moreFresh Target Breach Cards Hitting Black Market
A Bitcoin-powered marketplace is selling stolen card data in small batches, offering card validity guarantees, an RSA presentation reveals.
read moreSeculert wins Global Excellence Award for innovation in enterprise security
Company recognized for its Advanced Threat Protection solution
Santa Clara, Calif., February 25, 2014 – Seculert, a leading advanced threat protection solution provider, announced today that the company has received the bronze award in the Innovations in Enterprise Security category at the 10th Annual 2014 Global Excellence Awards ceremony.
read moreNeiman Marcus Hackers Set Off 60,000 Alerts While Bagging Credit Card Data
The hackers who raided the credit-card payment system of Neiman Marcus Group set off alerts on the company’s security systems about 60,000 times as they slunk through the network, according to an internal company investigation.
read moreOn-Demand Webinar: Operation Shin-Bet- The Corporate Security Implications
On-demand webinar: Learn about the targeted attack by pro-Palestinian hacktivists which compromised Middle Eastern government ministries.
read moreExclusive: France's Snecma targeted by hackers - researcher
French aerospace engine maker Snecma, a unit of Safran, was attacked by hackers who exploited a vulnerability in Microsoft Corp's Internet Explorer, according to a computer security researcher.
read moreNew zero-day bug in IE 10 exploited in active malware attack, MS warns
Exploit hosted on hacked, US-based website commandeers visitors' PCs.
read moreOn-Demand Webinar: Learn about recent developments in the world of advanced threats and how to address them effectively
On-demand webinar: Learn about recent developments in the world of advanced threats and how to address them effectively
read moreOn-Demand Webinar: Nip advanced threats in the bud and protect your company’s reputation
On-demand webinar: Nip Advanced Threats in the Bud and Protect your Company’s Reputation
read moreLook to Israel for new cybersecurity ideas, innovation, partnerships and inspiration
But the most memorable parts of CyberTech 2014 were the multiple visits to the start-up pavilion, which included new cybersecurity companies that are challenging the status quo.
read moreIsraeli defense computer hacked via tainted email: cyber firm
Hackers broke into an Israeli defense ministry computer via an email attachment tainted with malicious software that looked like it had been sent by the country's Shin Bet secret security service, an Israeli cyber security firm said on Sunday.
read moreA closer look at the Target malware, Part II
Yesterday’s story about the point-of-sale malware used in the Target attack has prompted a flood of analysis and reporting from antivirus and security vendors about related malware.
read moreA sneaky path into Target customers’ wallets
It was, in essence, a cybercriminal’s dream. For months, an amorphous group of Eastern European hackers had been poking around the networks of major American retailers, searching for loose portals that would take them deep into corporate systems.
read moreSeculert expands executive team
Leading Advanced Threat Protection Solution Provider Hires IT Security Veterans to Help Accelerate Company Growth
MENLO PARK, CA – December 19, 2013 – Seculert, a leading advanced threat protection solution provider, today announced the appointment of Richard Greene as president of field operations and Moshe Meiseles as vice president of research and development.
read moreCloud-Based Sandboxing: An Elevated Approach to Network Security
While the concept of sandboxing isn’t new, it wasn’t until a few years ago that it entered the mainstream network security vocabulary and enterprises began using on-premises sandboxing appliances to test suspicious executables for malware.
read moreData Theft Trojan Defeats Security Sandbox
Security researchers have spotted a new variant of the Sazoora data-theft Trojan employing nifty tricks to avoid security sandboxes.
read moreU.S. enterprises in path of data-hijacking Sazoora campaign, firm finds
Researchers have detected a new variant of Sazoora malware, a data-hijacking trojan that is currently targeting U.S. users as part of an international campaign.
read moreDexter payment card malware strikes South Africa
The Dexter code was linked to a series of attacks on point-of-sale systems in the UK, US and dozens of other countries towards the end of last year.
read moreInfosec Startup Seculert: "Today’s Latest Cybersecurity Device is Tomorrow’s Paperweight"
Of all the issues facing CIOs these days, probably none is more challenging than cybersecurity. Literally every day we hear news about major cyber attacks being discovered. And these attacks are not just limited to smaller companies or run of the mill DDoS attacks, but major network penetrations everywhere from Fortune 500 companies to the Pentagon and the US military.
read moreTop 100+ Cyber Security Blogs By Page Rank
Welcome to the Top 100+ Cyber Security Blogs. This list will continue to be updated and refined. I will be adding new metrics and ranking factors in the future that will help give a better overall ranking.
read moreProtecting Against Advanced Persistent Threats: Choosing A Security Solution
Advanced Persistent Threats (APTs) are a growing danger to all organizations. Unlike legacy malware, which operate opportunistically, APTs can persist undetected on a network for over a year, while the perpetuators behind them manipulate and steal valuable data and carry out their devious economic, political and social agendas.
read moreOn-demand - Why depending on malware prevention alone is no longer an option
Learn how to protect your network from APTs. Register to on-demand webinar.
read moreSeculert v2.0: New look, new features, new technology
PETACH-TIKVA, ISRAEL — Seculert, the cloud-based advanced threat protection solution, announced today the release of a new version of their service. The new version features the general availability of their Elastic Sandbox technology (previously in Beta), an updated application programming interface (API), and a stunning new user interface. This new release comes just before Seculert’s scheduled appearance at Black Hat USA 2013.
read moreSeculert partners with Sequoia Capital, raises $10M in Series B financing
PETACH-TIKVA, ISRAEL - Seculert, the cloud-based advanced threat protection company, announced today the closing of a $10 million Series B funding partnership with Sequoia Capital with participation from existing investor, Norwest Venture Partners (NVP). Gili Raanan, partner at Sequoia Capital, has joined Seculert’s Board of Directors along with existing investor Dror Nahumi of NVP, founding investor Yoav Andrew Leitersdorf of YL Ventures and industry veteran Benny Schnaider.
read moreSeculert Uncovers Magic Malware
Seculert researchers recently came across a malware sample they're calling "Magic," which had remained undetected on targeted machines for 11 months.
read moreSeculert Named SC Magazine 2013 Rookie Security Company of the Year Finalist
Cloud-Based Advanced Threat Detection Company Receives Industry Recognition as Growth Surges
PETACH-TIKVA, ISRAEL - Seculert, the cloud-based advanced threat detection company, today announced it has been named a finalist in the Rookie Security Company of the Year category, for the 2013 SC Magazine Awards. This category acknowledges vendors who are disrupting the industry with new approaches and solutions to fight the growing complexities of cyber attacks and IT security demands.
Seculert selected as SINET 16 Innovator to present at 2012 SINET Showcase
PETACH-TIKVA, ISRAEL - Seculert, the cloud-based advanced threat detection company, today announced that it has been selected as a SINET 16 Innovator and will present at the 2012 SINET Showcase, on Oct. 25 at the National Press Club in Washington D.C. The Security Innovation Network (SINET) is sponsored by the U.S. Department of Homeland Security Science & Technology Directorate and designed to advance innovation and enable collaboration between the public and private sectors to defeat global cybersecurity threats.
read moreSeculert brings Big Data analytics to forefront of malware detection
Seculert Sense Uses Crowdsourcing and Security Collaboration to Combat Advanced Persistent Threats
read morecategories
- chevron_right In the Media (82)
- chevron_right News & Media (82)
- chevron_right Resources (17)
- chevron_right Press Releases (12)
- chevron_right Webinars (9)
- chevron_right Blog (5)
- chevron_right White Papers (4)
- chevron_right Reports (3)
- chevron_right 2015 (2)
- chevron_right Events (2)
- chevron_right Product (2)
- chevron_right 451 Report (1)
- chevron_right Black Hat, Security Analytics (1)
- chevron_right Brochures & Datasheets (1)
- chevron_right Gateway Attack Detection (1)
- chevron_right In the News (1)
- chevron_right Javelin (1)
- chevron_right Javelin Attack Simulator (1)
- chevron_right Uncategorized (1)
recent post
-
An Acquisition is Akin to a Rollercoaster Ride
Feb 15, 2017 9:32:37 PM -
Let’s Hack an Election, Shall We?
Nov 2, 2016 1:55:28 AM -
Nymaim: Deep Technical Dive - Adventures in Evasive Malware
Oct 11, 2016 3:30:00 PM

